Each month, ‘Cyber Talk’ will include statistics on GUC’s Phish Alert Button usage and, occasionally, any relevant cybersecurity or Information Technology (IT) tips or updates. This month, our IT Department has provided a cybersecurity update for Multi-Factor Authentication and passwords.
 Changes Coming to Multi-Factor Authentication
Changes Coming to Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a security protocol used to ensure that the person who is signing into a computer, software, or website is actually the person they claim to be. It’s when you are required to give two forms of proof, such as a password and a confirmation code, in order to log in.
GUC has been using MFA for more than 15 years via RSA tokens and more recently requiring MFA for customers to manage their online accounts. In the Fall of 2020, we switched to Microsoft Tokens for employees to remotely use Microsoft Office. We are not alone. It’s become common for many banks, credit card companies, stores, and other websites to require MFA. Still, criminals try to find their way through, which is prompting Microsoft and GUC to require a higher level of authentication.
Starting in February, all GUC employees who use Microsoft Office 365 (Outlook, SharePoint, Word, etc.) will be required to use MFA both in and away from GUC facilities. Currently, when off-site, employees are required to authenticate using the Authenticator app or by entering a code sent via text, a voice call, or an email address. Very soon, employees who log in primarily at GUC locations will also have to use MFA. But that’s not the biggest change.
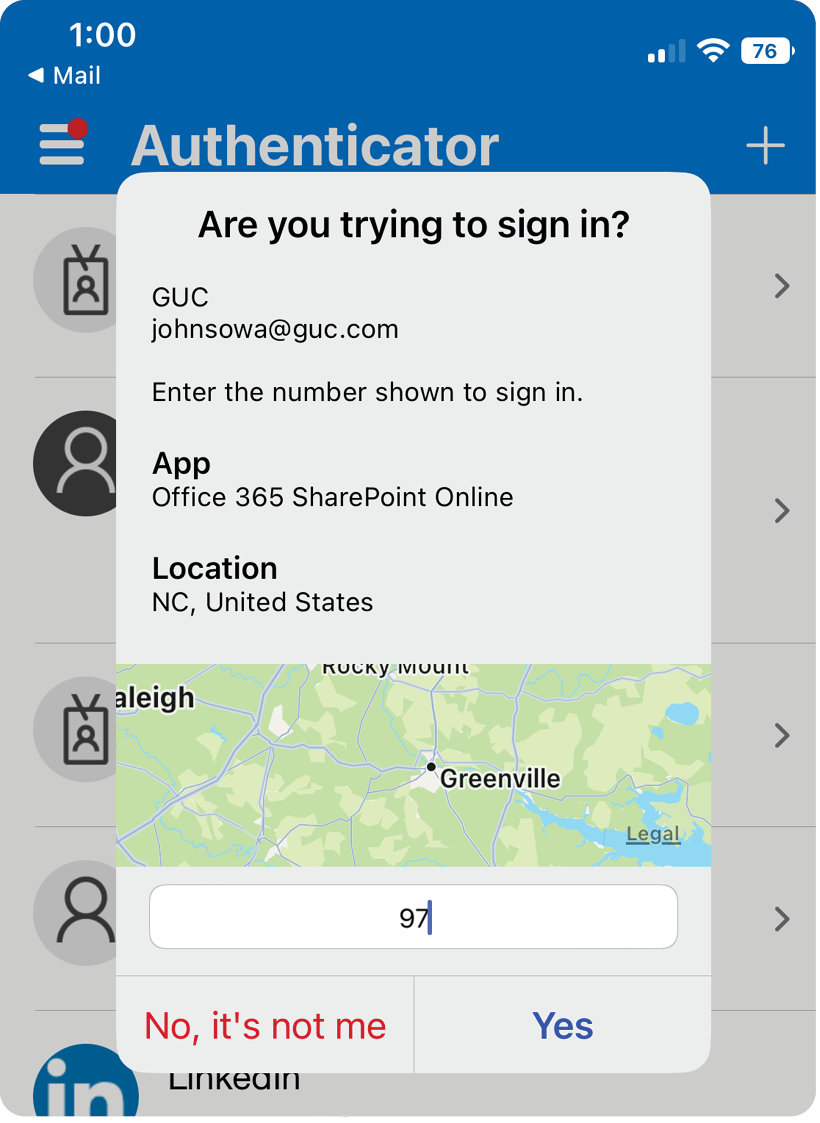
Beginning in February, the Authenticator app will also show a two-digit code that must be entered into the computer. As a bonus, the Authenticator app will show the name of the person trying to log in, the application they wish to use, and a map with a rough estimate of the location of the person requesting access. Note, the map is not precise, but generally within 75 miles. All of these new features serve to further secure and protect GUC from cyber threats.
If, for example, you are in Greenville and receive an authentication request on your phone and the map shows the request is coming from New York, you know it’s someone trying to log in from the New York area, pretending to be you. However, if you’re out of town and using GUC’s VPN (virtual private network), the map will show the request coming from Greenville, since that’s the location of the VPN.
For employees who authenticate using a code from text message, email, or a voice call, the only change will be the added requirement for authenticating when you’re on-site.
To further ensure our security, everyone will be required to authenticate every time they use a new computer. If you’re using a computer you log into regularly, you’ll likely only have to authenticate about every 90 days.
Remember, if you sign in from a shared computer such as in the training room, make sure you sign out when you are done. Otherwise, anybody can come along and use that computer with all the same permissions as you.
Password Policy Change
The Cybersecurity Task Force has recommended changes to the password requirements for system administrators. This is for people who log in to control systems such as SCADA, IT networks, and security systems.
People who log into these systems will now have to use longer passwords (25 or more characters) and must change them annually. IT will conduct audits quarterly to ensure passwords comply and that former GUC employees no longer have access to these systems.
TikTok
Governor Cooper issued an executive order on January 12th banning the social media app, TikTok, from all state-owned devices. Since GUC was established by the legislature, we fall under that order.
IT is working to remove TikTok from and banning its use on all GUC-owned devices.
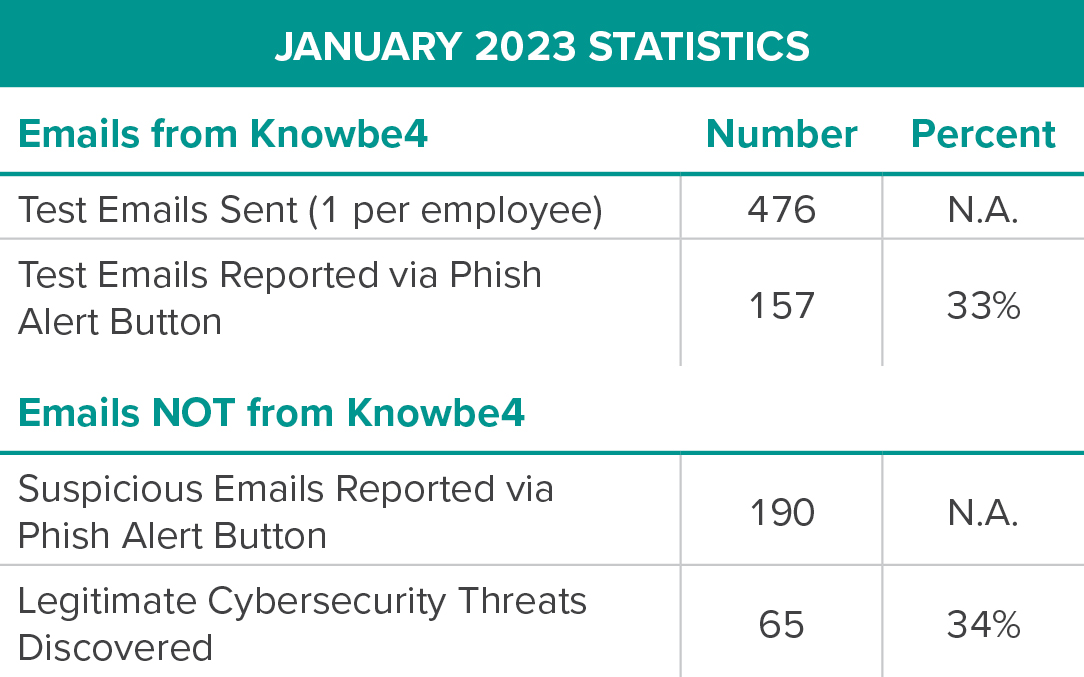
Phish Alert Button Statistics
IT is tracking use of the Phish Alert Button. The following statistics are from December 2022 and January 2023. Knowbe4 is the company that provides cyber training to GUC employees, and occasionally sends mock phish emails to test our cyber awareness.